harnessing the power of our people
After 2023 saw the industry's largest event of its kind welcome over 1000 attendees to The Brewery, London, we are very excited to once again define the future of engagement on 1st May 2024 at the 11th edition of the Employee Engagement Summit.
This year promises case studies, live interviews and panel discussions that showcase the importance of high-impact, purpose-driven employee engagement strategies through a lens that focuses on how organisational culture, collaboration, wellbeing and leadership buy-in are the the key to breeding high-performing, engaged teams.
Those that join us this year will have the chance to equip themselves with the tools needed to break the mould and create a people-centric culture where employees thrive.

Key facts
5 Content Stages
Round Table Sessions
15 Topic Streams
1000+ Delegates
Networking Party
70+ Presentations

WHAT TO EXPECT


















TOPIC STREAMS
Employee Engagement in the New World of Work
There has been a seismic shift in the way that we work over the last two years and many of these strategies are here to stay. This stream will highlight what the future of employee engagement looks like.
The Future of Employee Engagement
Our people are our biggest asset, so it’s crucial that we make sure that ‘work’ is a place that provides the experiences that will enable our people to thrive.
Effective Strategies for Employee Engagement
It’s so important to review and revise employee engagement strategies, so join this stream for innovative ideas relating to how to keep your people engaged.
Communication and Collaboration in the Modern Workplace
Communication and collaboration is increasingly taking centre stage in the quest for organisations to achieve higher and sustainable levels of employee engagement and productivity, particularly when employees are working remotely.
Wellbeing, Diversity & Inclusion
Probably the most crucial elements when it comes to employee engagement – join us to discover how to create a truly diverse, inclusive workplace where wellbeing takes centre stage.
Recruitment, Reward and Talent Retention
The great resignation has only highlighted the need to implement successful recruitment, reward and talent retention strategies. Join us to discover how to recruit the best talent and keep them engaged with your organisation.
Can Employee Experience Provide Competitive Advantage?
Our people are fast becoming the only way you will ever achieve a competitive advantage as, when we unlock the potential of our employees, we can drive customer experience to world class levels. Employees become our competitive advantage when they feel so engaged that they go above and beyond. Join this stream to discover how to unlock the potential of your employees.
Employee Engagement Strategy and Leadership
Employee engagement and productivity can only be achieved if the correct strategies are in place and we have inspirational role model leaders to effect and implement those strategies to move the organisation forward in an age of uncertainty and disruption.
CONTENT STAGES
Main Stage
The largest stage - here you can expect transformational case studies, exclusive fireside chats and in-depth panel discussions focusing on every aspect of employee engagement.
Communications & Collaboration
This stage will showcase those who are implementing communications strategies to achieve higher levels of employee engagement and productivity, regardless of location.
Reward, Wellbeing, Diversity & Inclusion
The most crucial elements when it comes to employee engagement – join us to discover how to create a truly diverse, inclusive workplace where wellbeing takes centre stage.
Strategy & Leadership
If your role relates to creating employee engagement strategies and leading initiatives, as well as gaining leadership buy-in, then this is the stage for you.
Organisational Culture
Discover the tools needed to create a people-centric culture which allows employees to thrive wherever they're working.

Ruby Wax
Ruby Wax OBE
Steve Clarke
Virgin Atlantic People Communications Lead
Christina Lewis
Deliveroo Gender Equity ERG Lead/ Head Of Global Rider Experience
Sarah Hood
Bupa Global Head of Engagement
Emma Illingworth
OVO Head of People TransformationA people centered, award winning, HR leader, with a track record of partnering Executive Leaders to design and deliver People Strategies. Led multiple large-scale acquisition, restructuring / efficiency, EVP and culture transformation programs.
Quick, creative thinker, calm under pressure, with a considered approach. Often described as an agitator and playmaker to achieve what can often feel like impossible change programmes. I thrive in bringing people together to co-create and deliver improved people's experiences.

Louisa McCabe
AXA Head of Internal CommunicationsWith several senior communication roles and an MA under my belt, my only regret is I didn't make the move sooner. I now spend my days doing what I love, connecting people with our leaders, sharing stories, celebrating the good stuff, and supporting people through the tough stuff.
Core skills include developing high performing teams, building and maintaining trust with senior stakeholders, strategic thinking, content development, campaign creation, writing, events, and change management.

Dev Mistry
Dojo Internal Communications and Engagement LeadPeople-focused communications are at the heart of Dev’s approach, no matter the size of maturity of the business. This is coupled with Dev’s proactive stance on inclusivity and equity within business processes, culture and communications, both from a personal and professional point of view. Outside of work, Dev also has a keen interest in initiatives supporting LGBTQ+ and BIPOC people respectively, through volunteer projects, cabaret performances and mentoring schemes.

Anaïs Nebel
Lipsy London Group Culture & Communications ManagerShe started her career in consulting before working for global retailers such as Estée Lauder Companies and The Body Shop. She has a unique understanding of internal and external brand experience - and how to make it resonate - having worked in marketing and customer experience before going into leadership development and people experience. In her current role, she looks after Wellbeing, Charity, Internal Comms, Employee Listening and Employer Branding.

Carlo Beschi
Treatwell Lead Agile CoachI help value flow.
An accomplished professional, with a very broad skill set and 15+ years of experience in digital product delivery, cultural change and organizational transformation.
I leverage on agile-lean practices to partner with leaders and teams, and help them improve their time to market, customer engagement, product quality and operational efficiency.
I love envisioning, strategizing, and executing - both individually and together with others.
I relentlessly cultivate a safe, vibrant, collaborative working environment, focussed on learning, engagement and innovation. A place where people grow, projects succeed, and business KPIs flourish - all at the same time.

Beth Perry
First Central Head of Internal Communications and CultureHey, I’m Beth, Head of Internal Communications and Culture at First Central Group. With over a decade’s experience in creative and strategic positions, I’m a firm believer that comms and culture go hand-in-hand to deliver an awesome colleague experience. In a nutshell, it’s about listening, seeing people as people, and combining this with data to inform a truly authentic and kick-ass plan…that everyone wants to be part of.
Since joining First Central Group, we’ve been making a name for ourselves culturally by ranking #22 in Glassdoor’s Best Places to Work UK 2024 list, #7 for 2023’s Best Places to Work Wellbeing list and #7 in Best Places for Women (Super Large) …just to name a few.
When I’m not at work, I’m normally planning my next adventure (or living one). From Rio Carnival to the Trans-Siberian Railway, I’m never a few months away from a plane or immersing myself into something new.
.png?width=400&name=Wendy%20Murphy%20(2).png)
Wendy Murphy
Exinity VP Corporate Communications
Melanie Page
Balfour Beatty Head of Group Innovation ProgrammesMelanie heads up 'My Contribution': Balfour Beatty's award-winning engagement programme that harnesses the enthusiasm, knowledge, and expertise of the workforce to crowd-source ideas, innovate and problem solve. My Contribution gives employees a voice and empowers them to make positive change through the creation of powerful solutions that drive strategic growth and help make Balfour Beatty a great place to work.

Jeremy Gautrey-Jones
RSPCA Assistant Director Employee Experience
Victoria Wilson
Royal Air Force (Ministry of Defence) Employee Engagement Team Manager
Michelle Sage
Royal Air Force (Ministry of Defence) Employee Engagement Advisor
Alix Ainsley
Virgin Group People DirectorAlix and Charlotte bring their experience and leadership to their current role, leading the people partnering and proposition teams. The ‘north star’ for the team is alignment to Virgin’s organisational purpose, this means investing in, developing, and inspiring the teams that are Changing Business for Good.

Charlotte Cherry
Virgin Group People DirectorAlix and Charlotte bring their experience and leadership to their current role, leading the people partnering and proposition teams. The ‘north star’ for the team is alignment to Virgin’s organisational purpose, this means investing in, developing, and inspiring the teams that are Changing Business for Good.

Emma Hughes
Phoenix Group Communication and Engagement of Colleague Representation ForumWith over 20 years’ experience of internal communication, specialising in bringing the colleague experience to life and integrating the colleague voice into people initiatives.
Emma and the PCRF team won the engage award for best use of Innovation in employee engagement in 2023.

Susan Reilly
Phoenix Group Head of Colleague RepresentationSusan Reilly is the Head of Phoenix Colleague Representation Forum, part of the Phoenix Group.
With over 15 years’ experience and a qualification in Employment Law, she is passionate about colleague engagement, building effective partnerships and the power of the colleague voice.
Susan specialises in colleague representation and progressive partnership working and loves utilising her skills and experience to create and promote industry leading representation propositions and it’s benefits in the modern workplace.
Susan created the PCRF in 2021 and they successfully won the engage award for best use of Innovation in employee engagement in 2023.
She lives near Edinburgh and loves spending time with her friends and family, particularly the latest addition to the family, her first grandchild.

Gabby Ogiste
Mars Veterinary Health International Lead, People Systems & Solutions
Neil Morrison
Severn Trent Group Human Resources DirectorTechnically, he has expertise in change management (especially digital transformation), compensation and benefits (including remuneration committees), organisational development, talent management, strategic resourcing, employee relations and communications. He's partnered with a range of CEOs and board members and contribute to the broader business leadership and strategy.
He prides himself on his communication skills and broad business knowledge. Down to earth, calm and measured whilst still working at pace and focused on delivery. The range of his experience means he's learnt to adapt and flex to different industries and cultures. he's also a qualified coach.
When he's not working, he is passionate about education, skills and the world of work in general. He's a regular commentator on leadership and management and has written for publications in the UK and US and spoken at conferences across the globe.

Tanai Vadera
Nando's Senior Product Manager
Debbie Events
Pluxee Client Service Manager
Connor Roche
Pluxee Business Development ManagerConnor is passionate about employee benefits and wellbeing. Dedicated to enhancing workplace satisfaction and productivity through tailored solutions. A trusted advisor with a focus on holistic employee wellness.

Helen Card
Homes England Head of Internal and Digital Communications
Parysa Hosseini-Sech
Onecom People & Culture Director
John Townsend
Unicef UK Head of Internal CommunicationsJohn believes passionately in the power of internal communications to set the tone for an organisation’s culture, leading to better places to work and ultimately better organisational results.

Neil Bestford
Byggfakta Group Group Director of Brand and People Experience
Henry Elworthy
John Lewis Partnership Channels LeadAt the John Lewis Partnership, he leads the team accountable for internal and external channels, events, planning, and leadership communications, as well as running a team of communicators charged with delivering fast-paced change communications. With 25 million hits to their intranet each year, over 70 sites and 550 communities to manage, there’s rarely a dull moment in his team.

Victoria Black
The Travel Chapter Head of Internal Communications
Dr Sarah Pass
Engage for SuccessSarah is a practitioner-focused academic concentrating on employee experience and engagement. Sarah is a member of the Engage for Success (EFS) Advisory Board. She also sits on the EFS steering group, chairs the East Midlands Area Network, the Line Managers TAG, the Engagement Champion TAG, and is the co-project lead for the EFS annual survey. In 2023, Sarah was ranked by HR Magazine as an Influential Thinker in HR. She is a Fellow of the RSA, an Academic Associate of the CIPD, and a member of the British Academy of Management. Sarah also sits on the Advisory Board for the EX-Space and is a member of the Involvement and Participation Association (IPA) Working Insights Group. Sarah currently works as a Senior Lecturer at Nottingham Business School (NTU).

James Court-Smith
Engage for Success
Chris Ronald
Blackhawk Network VP B2B EMEAChris is accountable for accelerating and enabling growth by creating high-performance teams and functions that work to scale the business. After holding leadership roles across both public and private companies for national and global brands, Chris has a wealth of experience when it comes to general management, sales & marketing, client success & service and operations. As a result, Chris is able to achieve strategic transformation and drive profitable B2B growth strategies for Blackhawk Network and its customers.

Owen Rose
Acteon Managing Partner
Jessica Brannigan
Culture Amp Lead People ScientistShe has over a decade of experience in the people and culture space encompassing in-house HR and workforce development roles, in-depth leadership assessment and coaching, human capital consulting and talent & career development. She enjoys combining these expertise to enhance workplace culture for the organisations we serve and the employees within them.
Prior to joining Culture Amp she led a programme at Oxford University’s Saïd Business School to enhance the leadership skills, and personal and career progression of MBA’s entering into high-profile careers. Thinking about the individual, their development and their trajectory within the sphere of an organisation is therefore of particular interest to her.

Caro Ruttledge
Gate One Partner
Jenna Brown
Uber for Business Head of Uber for Business, UK.png?width=400&name=Laura%20Jamieson%20headshot%20%20(5).png)
Laura Jamieson
Alshaya Group Head of Internal Communications.png?width=400&name=Duaa%20Almousawi%201%20(2).png)
Duaa Almousawi
Alshaya Group Internal Communications ExecutiveIn addition to my marketing experience, I’ve been working as a business owner and copywriter for quite some time. This has given me the chance to successfully connect my passion for marketing, my talent in writing, and my skills in business. I am also a Certified Image Consultant with an impeccable eye for detail.
Due to my social and friendly nature, I am a true team player, always happy and able to work with others. Additionally, I thrive under pressure and I like a good challenge. I believe that all of these traits make me a valuable asset to any team.
My aim is to continuously evolve my interpersonal, technical, and educational skills in order to truly make a change. I aspire to positively impact the people around me, and society as a whole, in the best way I possibly can.

Daniela Hoyos
Swissport Communications Manager
Ross Parker
Allianz Employee Engagement ManagerAn influential leader with over 10 years’ experience in the field of Employee Engagement, Wellbeing and Recognition.
Ross inspires and leads a network of Engagement Reps, Wellbeing Reps and Mental Health First Aiders to champion a culture where people matter, and voices are heard.
Following Allianz acquisition of LV= General Insurance, Ross is now using his expertise to roll out people strategies across Allianz Holdings.
Ross has led his past organisation to receive industry recognition as well leading project teams to scoop-up a number of internal awards too.

Evan Rhoda
Blackbaud Principal, Corporate Solutions
Alice Boyd
Firstup Lead Consultant - Communications StrategyCreative communications professional with a passion for people, storytelling, brand and culture.
I'm now partnering with Firstup customers to help drive adoption and engagement throughout their digital employee experience journeys. This includes reaching 100% of their workforce to drive business initiatives, boosting morale through employee recognition, and leveraging data insights to inform business decisions.
I've worked in various sectors in both New Zealand and the UK, including technology, utilities, and healthcare. Some of my specialties include internal engagement, digital employee communications, and stakeholder management.

Ulus Isa
Firstup Solutions Consultant
Caleb Chisholm
Cocentric Head of Digital ConsultingUsing his past experiences from leading internal digital engagement at NatWest, he has worked with a wide range of UK and International brands from manufacturing, to finance, and retail to professional services.
This work has included creating award winning campaigns and content, reviewing channel effectiveness, delivering strategic consultancy and launching digital communication and collaboration platforms.

Hillary Brown
Forty1 Managing DirectorWith previous roles including the Head of Group Campaigns and Head of Internal Communications for NatWest Markets, she has a deep understanding of how to navigate complex, matrixed, global organisations to deliver strategic communications with impact. Hillary has supported the growth of the practice, working with many industry leaders in professional services, industrial, financial services and pharmaceutical. She is incredibly passionate about data-led campaigns and the power of brilliant user experiences and creative execution to inspire lasting change.

Guy Champniss, PHD
Forty1/Inizio Engage XD Head of Behavioural Science
Harry Harvey
Klaxoon Sales DirectorHarry has a track record of supporting business-wide digital innovation projects that put people at the heart of the solution. He’s delivered solutions to a range of industries including Central Government, Utilities, and AEC. He currently leads the team in the UK, Nordics, and APAC markets for Klaxoon, the all-in-one collaboration platform. Harry works with teams worldwide to provide solutions that make business easy (and accessible) for everyone, increase productivity and drive positive outcomes.

Kaz Hassan
Unily Employee Experience Industry Lead
Matt Phelan
The Happiness Index CEO & Founder
Dave Nixon
LumApps Employee Experience Practice ManagerDave has guided organisations on their journey to creating vibrant, user-centric digital workplaces that drive productivity and enhance communication for over 20 years.
Dave is experienced in developing and executing strategies that drive adoption and maximize the potential of intranet platforms that include SharePoint, Jive, and LumApps
As a thought leader in the field, Dave has successfully guided numerous enterprises through the intricacies of intranet implementation, ensuring a user-centric approach that goes beyond mere functionality.
Recognized for a keen ability to translate complex technical concepts into user-friendly solutions, Dave is dedicated to creating intranet experiences that not only streamline workflows but also elevate employee engagement to new heights.

Josh Bean
Zendesk Employee Experience Business Lead
Tom Nash
Pluxee HR Business PartnerHe has been with Pluxee for 3 years supporting the business to continuously enhance the employee experience and drive high performance through the people plan for the commercial, marketing, and partnership business.
Tom has a strong focus on connecting people initiatives with commercial outcomes and has a deep passion for wellbeing and resilience.

Burcin Ressamoglu
Pluxee CEOHer dedication extends beyond business growth to nurturing individuals, empowering both seasoned executives and emerging talent to reach their full potential.
Burcin is devoted to promoting sustainability initiatives within Pluxee UK and is an advocate for Diversity, Equity, and Inclusion. She is actively involved in shaping gender equality policies as a member of the Sodexo Global Gender Equality Advisory Board – SoTogether.

Jo Moffatt
Engage for Success Strategy DirectorJo has been a volunteer with the Engage for Success movement since its launch. As Strategy Director she sits on the Core Team and co-hosts the weekly Engage for Success radio show. EFS radio draws guests from across the engagement world with interesting stories to share. The Engage for Success agenda is absolutely aligned with Jo’s vision ‘to make workplaces better places to be’. Jo’s ‘day job’ is MD and founder of Woodreed, a specialist ad agency who use the tools, techniques, creativity and insight of the advertising world to engage employees inside organisations. Jo is passionate about brands and their power to move people. She is equally passionate about employee engagement and its vital role in delivering a high performing organisation. Put the two together and she becomes almost evangelical about the power a well-positioned and consistently delivered brand has as a catalyst for employee engagement and business success.
Charlotte Dahl
Woodreed Creative Planning Director
Cathy Brown
Handley Studios Ltd. Co-FounderCathy (she/her) works with people and organisations to create inclusive, healthy and more productive workplaces that work for everyone.
A renowned leader, speaker and communicator, Cathy blends curiosity and empathy with deep cross-sector experience. She prides herself on helping people move out of stressful situations to create human-focused workplace cultures where compassion and connectedness – and people – are encouraged and valued.
Cathy has led organisations across a range of industries including Engage for Success (the UK’s movement for Employee Engagement), and has helped to transform many more through her work as Capability Brown, and most recently at Management Geek.
Cathy carries her personal experience of neurodivergence into the solutions she co-creates with her clients, through conversations, commitment and curiosity - helping them to manage themselves and their teams in ways that work for everyone.
.png?width=400&name=Project%20(55).png)
Jo Dodds
Engage for Success Co-Strategy DirectorAs co-Strategy Director of Engage for Success, Jo is focused on spreading the word about employee engagement and shining a light on good practise, inspiring people and workplaces to thrive. She also co-hosts the long running weekly Engage for Success radio podcast talking all things employee engagement with a wide range of guests from all over the world. Her corporate background is in regional and national HR and training roles within large retail and leisure organisations. She started her own business in 2005 and has since worked with people and organisations to take advantage of the digital and social media opportunities to create engagement with customers, employees and other stakeholders.

Nicholas Brice
Soul Corporations CEO
9.00-9.10
Opening Remarks
Speaker:

Jo Moffatt
Engage for SuccessStrategy Director
Jo has been a volunteer with the Engage for Success movement since its launch. As Strategy Director she sits on the Core Team and co-hosts the weekly Engage for Success radio show. EFS radio draws guests from across the engagement world with interesting stories to share. The Engage for Success agenda is absolutely aligned with Jo’s vision ‘to make workplaces better places to be’. Jo’s ‘day job’ is MD and founder of Woodreed, a specialist ad agency who use the tools, techniques, creativity and insight of the advertising world to engage employees inside organisations. Jo is passionate about brands and their power to move people. She is equally passionate about employee engagement and its vital role in delivering a high performing organisation. Put the two together and she becomes almost evangelical about the power a well-positioned and consistently delivered brand has as a catalyst for employee engagement and business success.
9:10 - 9:25
Opening Keynote: The Current State of Employee Engagement
Findings indicate engagement levels still lag significantly behind pre-pandemic levels, with no change in the EFS engagement index. Although the figures are concerning, the data highlights variations in engagement levels and presents key areas for action. A key observation is the need to push the people issues up the agenda. Hear about variations in organisational size and sector, and the impact of hybrid working and health and wellbeing on engagement.
During the session, we will explore:
• The current state of employee engagement in the UK
• Discuss the Engage for Success Employee Engagement Index benchmark
• Explore variations in engagement levels and what this means to practice
Speakers:

Dr Sarah Pass
Engage for SuccessSarah is a practitioner-focused academic concentrating on employee experience and engagement. Sarah is a member of the Engage for Success (EFS) Advisory Board. She also sits on the EFS steering group, chairs the East Midlands Area Network, the Line Managers TAG, the Engagement Champion TAG, and is the co-project lead for the EFS annual survey. In 2023, Sarah was ranked by HR Magazine as an Influential Thinker in HR. She is a Fellow of the RSA, an Academic Associate of the CIPD, and a member of the British Academy of Management. Sarah also sits on the Advisory Board for the EX-Space and is a member of the Involvement and Participation Association (IPA) Working Insights Group. Sarah currently works as a Senior Lecturer at Nottingham Business School (NTU).

James Court-Smith
Engage for Success
09:25 - 09:25
Unlock the Future of Intelligent Employee Experiences With Zendesk and Nando’s
Speakers:

Josh Bean
ZendeskEmployee Experience Business Lead

Tanai Vadera
Nando'sSenior Product Manager
9:45 - 10:10
Ruby Wax OBE: How to De-Frazzle in a Chaotic World
Actress, comedian, mental health campaigner and award-winning author Ruby Wax is one of the most highly regarded mental health speakers in the industry, removing taboo from the topic and inspiring audiences globally.
Awarded an OBE for her services to mental health, Ruby has enjoyed an influential career in the media, and now utilises her comedic talents to break down the stigma surrounding mental health.
Ruby will be sharing her incredible insights on how to deal with stress, improve wellbeing and mental health, and become the driver – not the driven – when it comes to matters of the mind.
Speaker:

Ruby Wax
Ruby Wax OBE
10:10 - 10:30
Employee Engagement: Connecting Your Workforce with Travel Chapter & Cocentric
Speakers:

Caleb Chisholm
CocentricHead of Digital Consulting
Using his past experiences from leading internal digital engagement at NatWest, he has worked with a wide range of UK and International brands from manufacturing, to finance, and retail to professional services.
This work has included creating award winning campaigns and content, reviewing channel effectiveness, delivering strategic consultancy and launching digital communication and collaboration platforms.

Victoria Black
The Travel ChapterHead of Internal Communications
10:30 - 11:00
Coffee & Networking
11:00 - 11:20
The Business of Motivation: Understanding What Drives Us – And How It Can Be Your Best Source of Competitive Advantage
In this session – featuring findings from our latest study – we’ll share a state-of-the-nation view of motivation at work, get under the skin of what really motivates a modern workforce and examine what we can do to ensure our teams are motivated to perform at their best.
We’ll dig into why our assumptions about motivation in the workplace are often misplaced, explore its complex and dynamic nature, and how achieving a motivational balance can unlock even greater human potential – and better organisational performance.
Speakers:

Hillary Brown
Forty1Managing Director
With previous roles including the Head of Group Campaigns and Head of Internal Communications for NatWest Markets, she has a deep understanding of how to navigate complex, matrixed, global organisations to deliver strategic communications with impact. Hillary has supported the growth of the practice, working with many industry leaders in professional services, industrial, financial services and pharmaceutical. She is incredibly passionate about data-led campaigns and the power of brilliant user experiences and creative execution to inspire lasting change.

Guy Champniss, PHD
Forty1/Inizio Engage XDHead of Behavioural Science
11:20 - 11:40
People & Culture - Engagement Strategies for a Modern Workplace
Join our exclusive panel discussion to learn how organisations are adapting to meet the needs of both a modern workplace and workforce.
We'll be looking at:
- Technology-driven strategies to allow us to better connect employees- Communication initiatives that can enhance employee engagement in a hybrid world
- Embedding a culture of belonging regardless of physical location
- The changing needs of a new generation of employees
- Recognition and appreciation and creating a culture of gratitude when employees are not always together
- Building a sense of camaraderie and belonging among employees
- Learning and Development initiatives
- Actionable insights that attendees can take home and implement
Speakers:

Gabby Ogiste
Mars Veterinary HealthInternational Lead, People Systems & Solutions

Helen Card
Homes EnglandHead of Internal and Digital Communications

Beth Perry
First CentralHead of Internal Communications and Culture
Hey, I’m Beth, Head of Internal Communications and Culture at First Central Group. With over a decade’s experience in creative and strategic positions, I’m a firm believer that comms and culture go hand-in-hand to deliver an awesome colleague experience. In a nutshell, it’s about listening, seeing people as people, and combining this with data to inform a truly authentic and kick-ass plan…that everyone wants to be part of.
Since joining First Central Group, we’ve been making a name for ourselves culturally by ranking #22 in Glassdoor’s Best Places to Work UK 2024 list, #7 for 2023’s Best Places to Work Wellbeing list and #7 in Best Places for Women (Super Large) …just to name a few.
When I’m not at work, I’m normally planning my next adventure (or living one). From Rio Carnival to the Trans-Siberian Railway, I’m never a few months away from a plane or immersing myself into something new.
11:40 - 12:00
Fuelling Success: The Impact of Wellbeing on Employee Performance
Join us as we delve into the crucial connection between employee wellbeing and performance. We will explore how prioritising employee wellbeing leads to enhanced productivity, reduced absenteeism, elevated job satisfaction, and high-performing teams. We will analyse our latest whitepapers and industry research to illustrate the direct impact of financial, mental, and physical wellbeing on individual and team performance. Attendees will discover valuable insights on how to cultivate a workplace culture that prioritises employee wellbeing, leading to measurable improvements in performance.
Speakers:

Burcin Ressamoglu
PluxeeCEO
Her dedication extends beyond business growth to nurturing individuals, empowering both seasoned executives and emerging talent to reach their full potential.
Burcin is devoted to promoting sustainability initiatives within Pluxee UK and is an advocate for Diversity, Equity, and Inclusion. She is actively involved in shaping gender equality policies as a member of the Sodexo Global Gender Equality Advisory Board – SoTogether.

Tom Nash
PluxeeHR Business Partner
He has been with Pluxee for 3 years supporting the business to continuously enhance the employee experience and drive high performance through the people plan for the commercial, marketing, and partnership business.
Tom has a strong focus on connecting people initiatives with commercial outcomes and has a deep passion for wellbeing and resilience.
12:00 - 12:20
Engagement in the Eye of the Storm: A Fireside Chat with Neil Morrison, HR Director at Severn Trent
Speaker:

Neil Morrison
Severn TrentGroup Human Resources Director
Technically, he has expertise in change management (especially digital transformation), compensation and benefits (including remuneration committees), organisational development, talent management, strategic resourcing, employee relations and communications. He's partnered with a range of CEOs and board members and contribute to the broader business leadership and strategy.
He prides himself on his communication skills and broad business knowledge. Down to earth, calm and measured whilst still working at pace and focused on delivery. The range of his experience means he's learnt to adapt and flex to different industries and cultures. he's also a qualified coach.
When he's not working, he is passionate about education, skills and the world of work in general. He's a regular commentator on leadership and management and has written for publications in the UK and US and spoken at conferences across the globe.
12:20 - 12:40
How Alshaya Group is activating the world’s biggest brands
Speakers:
.png?width=200&name=Laura%20Jamieson%20headshot%20%20(5).png)
Laura Jamieson
Alshaya GroupHead of Internal Communications
.png?width=200&name=Duaa%20Almousawi%201%20(2).png)
Duaa Almousawi
Alshaya GroupInternal Communications Executive
In addition to my marketing experience, I’ve been working as a business owner and copywriter for quite some time. This has given me the chance to successfully connect my passion for marketing, my talent in writing, and my skills in business. I am also a Certified Image Consultant with an impeccable eye for detail.
Due to my social and friendly nature, I am a true team player, always happy and able to work with others. Additionally, I thrive under pressure and I like a good challenge. I believe that all of these traits make me a valuable asset to any team.
My aim is to continuously evolve my interpersonal, technical, and educational skills in order to truly make a change. I aspire to positively impact the people around me, and society as a whole, in the best way I possibly can.

Kaz Hassan
UnilyEmployee Experience Industry Lead
12:40 - 13:40
Lunch & Networking
13:35-13:40
Afternoon Remarks
Speaker:
Charlotte Dahl
WoodreedCreative Planning Director
13:40 - 14:00
AXA Case Study - Embracing Breakthrough Thinking to Drive Engagement
- Adopted breakthrough thinking to generate innovative and unconventional ideas
- Exceeded expectations of results from landing our new strategy
- Created advocates for our new brand campaign
Speaker:

Louisa McCabe
AXAHead of Internal Communications
With several senior communication roles and an MA under my belt, my only regret is I didn't make the move sooner. I now spend my days doing what I love, connecting people with our leaders, sharing stories, celebrating the good stuff, and supporting people through the tough stuff.
Core skills include developing high performing teams, building and maintaining trust with senior stakeholders, strategic thinking, content development, campaign creation, writing, events, and change management.
14:00 - 14:20
Virgin Group Case Study: Crafting Awesome Employee Experiences
Join Gate One's Caro Ruttledge and Virgin Group's Alix Ainsley and Charlotte Cherry to explore how Virgin Group have approached this and lessons for other organisations, to unlock greater connection, innovation and success.
Speakers:

Caro Ruttledge
Gate OnePartner

Alix Ainsley
Virgin GroupPeople Director
Alix and Charlotte bring their experience and leadership to their current role, leading the people partnering and proposition teams. The ‘north star’ for the team is alignment to Virgin’s organisational purpose, this means investing in, developing, and inspiring the teams that are Changing Business for Good.

Charlotte Cherry
Virgin GroupPeople Director
Alix and Charlotte bring their experience and leadership to their current role, leading the people partnering and proposition teams. The ‘north star’ for the team is alignment to Virgin’s organisational purpose, this means investing in, developing, and inspiring the teams that are Changing Business for Good.
14:20 - 14:40
Grass Roots: Harnessing Employee-Driven Engagement: A Fireside Chat with Christina Lewis, Head of Rider Experience at Deliveroo
In a time where resources are increasingly tight and understanding the experiences of underrepresented groups is imperative- ERG’s may be the employee engagement resource you didn’t realise you needed.
Hear from Christina Lewis, Deliveroo’s Gender Equity ERG lead and award-winning ‘WiHTL Woman To Watch 2024’ on how ERG groups can boost company culture & employee engagement, drive impact for underrepresented groups, give grassroot insight, as well as the pitfalls to avoid.
Speaker:

Christina Lewis
DeliverooGender Equity ERG Lead/ Head Of Global Rider Experience
14:40 - 15:00
Navigating Change: Leveraging Engagement and Employee Experience for Organizational Success?
Speaker:

Jessica Brannigan
Culture AmpLead People Scientist
She has over a decade of experience in the people and culture space encompassing in-house HR and workforce development roles, in-depth leadership assessment and coaching, human capital consulting and talent & career development. She enjoys combining these expertise to enhance workplace culture for the organisations we serve and the employees within them.
Prior to joining Culture Amp she led a programme at Oxford University’s Saïd Business School to enhance the leadership skills, and personal and career progression of MBA’s entering into high-profile careers. Thinking about the individual, their development and their trajectory within the sphere of an organisation is therefore of particular interest to her.
15:00 - 15:30
Coffee & Networking
15:30 - 15:45
Virgin Atlantic Case Study: Navigating the Social Workplace: The Rise of Video to Superpower Engagement
Here, Steve will share how his communications team has evolved its approach and skillset to focus on mobile first, video storytelling and live events, how they brought the Virgin Atlantic leadership team along for the ride, and the positive impact this is having on engagement and happiness.
Speaker:

Steve Clarke
Virgin AtlanticPeople Communications Lead
15:45 - 16:00
Transforming Workplaces in the Face of Global Growth: A Fireside Chat With Neil Bestford of Byggfakta Group
In this fireside chat, Neil Bestford, Director of Brand and People Experience at Byggfakta Group, shares valuable insights into transforming engagement and culture. He joins Interact Software’s Jemma Goodman to discuss:
- Strategies for creating a cohesive culture at a fast-growing, global organisation
- The best ways to educate leadership and roll out new people and culture initiatives
- His experience combining several disjointed, decentralised platforms and channels into a single source of truth in a short timeframe
- How to build out a robust comms strategy with a lean team
Speaker:

Neil Bestford
Byggfakta GroupGroup Director of Brand and People Experience
16:00 - 16:30
Lipsy London Case Study: Rethinking Wellbeing: When a Fashion Group Empowered Confidence Inside-Out
Body image is a huge issue in today’s society: 91% of women say they're unhappy with the way they look and Facetune (the number one editing app) has been downloaded over 200 millions times globally.
In a world where people are struggling with their self-esteem, Wellbeing shouldn’t be a corporate tick box exercise. It should genuinely give people opportunities to feel empowered, supported, and cared for. Especially in industries like Fashion and Beauty.
In this talk, Anaïs Nebel will share why the British fashion group Lipsy added self-empowerment to their Wellbeing strategy, and how they launched it with a 4-day self-portrait event that increased employee’s feeling of self-empowerment by 40%…
Speaker:

Anaïs Nebel
Lipsy LondonGroup Culture & Communications Manager
She started her career in consulting before working for global retailers such as Estée Lauder Companies and The Body Shop. She has a unique understanding of internal and external brand experience - and how to make it resonate - having worked in marketing and customer experience before going into leadership development and people experience. In her current role, she looks after Wellbeing, Charity, Internal Comms, Employee Listening and Employer Branding.
16:30 - 17:00
Harnessing the Power of our People: Overcoming Challenges and Seizing Opportunities
Looking towards the future, we'll also explore how the employee engagement landscape is changing, what plans our panelists have in place for the future and what's next for the industry.
Speakers:

Dev Mistry
DojoInternal Communications and Engagement Lead
People-focused communications are at the heart of Dev’s approach, no matter the size of maturity of the business. This is coupled with Dev’s proactive stance on inclusivity and equity within business processes, culture and communications, both from a personal and professional point of view. Outside of work, Dev also has a keen interest in initiatives supporting LGBTQ+ and BIPOC people respectively, through volunteer projects, cabaret performances and mentoring schemes.

Sarah Hood
BupaGlobal Head of Engagement

Melanie Page
Balfour BeattyHead of Group Innovation Programmes
Melanie heads up 'My Contribution': Balfour Beatty's award-winning engagement programme that harnesses the enthusiasm, knowledge, and expertise of the workforce to crowd-source ideas, innovate and problem solve. My Contribution gives employees a voice and empowers them to make positive change through the creation of powerful solutions that drive strategic growth and help make Balfour Beatty a great place to work.

Parysa Hosseini-Sech
OnecomPeople & Culture Director
13:35-13:40
Host Welcome
Jo welcomes attendees to the Organisational Culture Breakout Stage.
Speaker:

Jo Moffatt
Engage for SuccessStrategy Director
Jo has been a volunteer with the Engage for Success movement since its launch. As Strategy Director she sits on the Core Team and co-hosts the weekly Engage for Success radio show. EFS radio draws guests from across the engagement world with interesting stories to share. The Engage for Success agenda is absolutely aligned with Jo’s vision ‘to make workplaces better places to be’. Jo’s ‘day job’ is MD and founder of Woodreed, a specialist ad agency who use the tools, techniques, creativity and insight of the advertising world to engage employees inside organisations. Jo is passionate about brands and their power to move people. She is equally passionate about employee engagement and its vital role in delivering a high performing organisation. Put the two together and she becomes almost evangelical about the power a well-positioned and consistently delivered brand has as a catalyst for employee engagement and business success.
13:40 - 14:00
OVO Case Study: The OVO Effect - Culture Creation
Speaker:

Emma Illingworth
OVOHead of People Transformation
A people centered, award winning, HR leader, with a track record of partnering Executive Leaders to design and deliver People Strategies. Led multiple large-scale acquisition, restructuring / efficiency, EVP and culture transformation programs.
Quick, creative thinker, calm under pressure, with a considered approach. Often described as an agitator and playmaker to achieve what can often feel like impossible change programmes. I thrive in bringing people together to co-create and deliver improved people's experiences.
14:00 - 14:20
How Allianz Used Recognition to Support a Change in the Values Across Their Organisation
Join us for this fireside chat and discover how Achievers’ customer, Allianz, utilised recognition to drive cultural transformation. Learn practical insights on aligning values and boosting employee engagement and gain actionable strategies to implement high adoption recognition programs.
Speakers:

Alyssa Tantillo
AchieversSolutions Consultant

Ross Parker
AllianzEmployee Engagement Manager
An influential leader with over 10 years’ experience in the field of Employee Engagement, Wellbeing and Recognition.
Ross inspires and leads a network of Engagement Reps, Wellbeing Reps and Mental Health First Aiders to champion a culture where people matter, and voices are heard.
Following Allianz acquisition of LV= General Insurance, Ross is now using his expertise to roll out people strategies across Allianz Holdings.
Ross has led his past organisation to receive industry recognition as well leading project teams to scoop-up a number of internal awards too.
14:20 - 14:40
Royal Air Force Case Study: Developing an Employee Engagement Champions Network
In 2019, we sat in delegate seats, taking notes on speakers, to learn and implement their findings for us to start our employee engagement journey. We wanted to make a difference, but working in Government, and the financial challenges that are faced, we had to do this at low or no cost. We wanted to show that the annual People Surveys, and action plans will, and do make a difference to employee working lives. It’s been a long journey, and at times frustrating, but we seeing great improvements.
We are delighted to be invited to present to you on our journey - our challenges, successes, and who helped us along the way, from when we started out, where we are today and where we want to be.
Speakers:

Victoria Wilson
Royal Air Force (Ministry of Defence)Employee Engagement Team Manager

Michelle Sage
Royal Air Force (Ministry of Defence)Employee Engagement Advisor
14:40 - 15:00
Why Today’s Emotions = Tomorrow’s Performance
Matt Phelan - co-founder and CEO of The Happiness Index, uncovers the factors that drive employee engagement and happiness at work, and explores how organisations can create a thriving workplace culture that enables their people to succeed.
Speaker:

Matt Phelan
The Happiness IndexCEO & Founder
15:00 - 15:30
Coffee & Networking
13:35-13:40
Host Welcome
Speaker:
.png?width=200&name=Project%20(55).png)
Jo Dodds
Engage for SuccessCo-Strategy Director
As co-Strategy Director of Engage for Success, Jo is focused on spreading the word about employee engagement and shining a light on good practise, inspiring people and workplaces to thrive. She also co-hosts the long running weekly Engage for Success radio podcast talking all things employee engagement with a wide range of guests from all over the world. Her corporate background is in regional and national HR and training roles within large retail and leisure organisations. She started her own business in 2005 and has since worked with people and organisations to take advantage of the digital and social media opportunities to create engagement with customers, employees and other stakeholders.
13:40 - 14:00
Homes England Case Study: Engaging Your People in Transformation and Change, Through One Coherent Story
This session will use a live example of how this is currently being delivered, what’s worked, what were the challenges and how these were overcome.
Speaker:

Helen Card
Homes EnglandHead of Internal and Digital Communications
14:00 - 14:20
Why Personalised Communications Is the Key to Employee Engagement at Swissport
Speaker:

Daniela Hoyos
SwissportCommunications Manager
14:40 - 15:00
John Lewis Partnership Case Study: Putting Users at the Heart of Your Intranet
From the bustling shop floor to the serene greens of its very own farm, the UK’s largest employee-owned business – the John Lewis Partnership – is no ordinary enterprise. So how do you keep its 70,000 co-owners informed, engaged and up-to-date through a period of significant transformation?
Find out how the Partnership doubled the readership of its strategic communications and curated an ecosystem with millions of interactions each year by putting users at the heart of its design.
Whether its:
- Reaching Partners before the press – rapidly reaching thousands of employees in the palm of their hands;
- Pushing productivity – with 4.5 million searches each year, making information easy to find is good business logic;
- Creating a personalised product – tailoring interactions to each employee’s role and interests;
- Fostering hundreds of communities to inspire, engage and connect its workforce.
Get an exclusive preview of their platform, and learn more about how they’re transforming digital experiences to be so much more than a site filled with policies and top-down news.
Speakers:

Henry Elworthy
John Lewis PartnershipChannels Lead
At the John Lewis Partnership, he leads the team accountable for internal and external channels, events, planning, and leadership communications, as well as running a team of communicators charged with delivering fast-paced change communications. With 25 million hits to their intranet each year, over 70 sites and 550 communities to manage, there’s rarely a dull moment in his team.

Dave Nixon
LumAppsEmployee Experience Practice Manager
Dave has guided organisations on their journey to creating vibrant, user-centric digital workplaces that drive productivity and enhance communication for over 20 years.
Dave is experienced in developing and executing strategies that drive adoption and maximize the potential of intranet platforms that include SharePoint, Jive, and LumApps
As a thought leader in the field, Dave has successfully guided numerous enterprises through the intricacies of intranet implementation, ensuring a user-centric approach that goes beyond mere functionality.
Recognized for a keen ability to translate complex technical concepts into user-friendly solutions, Dave is dedicated to creating intranet experiences that not only streamline workflows but also elevate employee engagement to new heights.
14:20 - 14:40
Powerful & Transformative Internal Communications: A Fireside Chat with John Townsend, Head of Internal Communications at Unicef UK
Speaker:

John Townsend
Unicef UKHead of Internal Communications
John believes passionately in the power of internal communications to set the tone for an organisation’s culture, leading to better places to work and ultimately better organisational results.
15:00 - 15:30
Coffee & Networking
13:35-13:40
Host Welcome
Speaker:

Nicholas Brice
Soul CorporationsCEO
13:40 - 14:00
Treatwell Case Study: Mergers, Acquisitions and Employee Engagement: The Role of Company Values
Speaker:

Carlo Beschi
TreatwellLead Agile Coach
I help value flow.
An accomplished professional, with a very broad skill set and 15+ years of experience in digital product delivery, cultural change and organizational transformation.
I leverage on agile-lean practices to partner with leaders and teams, and help them improve their time to market, customer engagement, product quality and operational efficiency.
I love envisioning, strategizing, and executing - both individually and together with others.
I relentlessly cultivate a safe, vibrant, collaborative working environment, focussed on learning, engagement and innovation. A place where people grow, projects succeed, and business KPIs flourish - all at the same time.
14:00 - 14:20
Speak to the Human: Moving From Strategy and Plans To Engagement and Impact
How do organisations like Channel 4 and Netflix create meaningful engagement for their people? Teams and organisations thrive when they unite a group of humans around shared purpose and values. We do our best work when we feel connected, engaged, and motivated. When we belong.
But it’s hard to build cohesion in a rapidly changing environment. Organisations are grappling with a range of issues that challenge connection and belonging, including remote working, the anticipated impacts of AI, portfolio careers and mercurial Gen Z-ers!
So how do you help individuals engage with business vision, strategy and plans? How do you create connections between colleagues, and motivation behind a shared purpose? And how do you foster that sense of belonging that leads the humans in your organisation to feel “this matters to me”?
This talk will cover:
- How to move from strategy and plans to engagement and impact.
- Identifying and prioritising the moments that really matter.
- Using a behavioural approach to deliver the greatest impact.
- Creating powerful communication to sustain engagement.
And we’ll be exploring ideas through practical case study examples.
Speaker:

Owen Rose
ActeonManaging Partner
14:20 - 14:40
Phoenix Group Case Study: Representing the Colleague Voice in the Modern Workplace
Today’s colleagues expect to have a say, at the earliest stages of decision making, when their working environment is impacted by change. So, how do we engage colleagues, and view their ideas and feedback as solutions? And why is it important for colleagues to recognise the direct link between their role and the strategic objectives of their organisation?
We believe the solution is to create effective partnerships between colleagues and the business, co-ordinated by an effective colleague representation forum.
We’ll be talking about our journey to creating and embedding an industry leading colleague representation forum, how we overcame challenges and how it benefits today’s colleagues and leaders.
Come and hear us talk about a progressive, innovate and alternative solution to colleague representation in the modern workplace.
Speakers:

Emma Hughes
Phoenix GroupCommunication and Engagement of Colleague Representation Forum
With over 20 years’ experience of internal communication, specialising in bringing the colleague experience to life and integrating the colleague voice into people initiatives.
Emma and the PCRF team won the engage award for best use of Innovation in employee engagement in 2023.

Susan Reilly
Phoenix GroupHead of Colleague Representation
Susan Reilly is the Head of Phoenix Colleague Representation Forum, part of the Phoenix Group.
With over 15 years’ experience and a qualification in Employment Law, she is passionate about colleague engagement, building effective partnerships and the power of the colleague voice.
Susan specialises in colleague representation and progressive partnership working and loves utilising her skills and experience to create and promote industry leading representation propositions and it’s benefits in the modern workplace.
Susan created the PCRF in 2021 and they successfully won the engage award for best use of Innovation in employee engagement in 2023.
She lives near Edinburgh and loves spending time with her friends and family, particularly the latest addition to the family, her first grandchild.
14:40 - 15:00
Using Human-Centric Work Models to Boost Employee Experience, Retain Talent, and Drive Performance
- The Human Centric Work Model and Why is it Back in the Spotlight?
- The New Work Culture Value Proposition: What do companies need to do to attract, retain and engage employees ?
- Leveraging Human Centric Management for Talent Retention
- Video Demonstration of Klaxoon
- Use Case
- Question & Answer
Speaker:

Harry Harvey
KlaxoonSales Director
Harry has a track record of supporting business-wide digital innovation projects that put people at the heart of the solution. He’s delivered solutions to a range of industries including Central Government, Utilities, and AEC. He currently leads the team in the UK, Nordics, and APAC markets for Klaxoon, the all-in-one collaboration platform. Harry works with teams worldwide to provide solutions that make business easy (and accessible) for everyone, increase productivity and drive positive outcomes.
15:00 - 15:30
Coffee & Networking
13:35-13:40
Host Welcome
Speaker:

Cathy Brown
Handley Studios Ltd.Co-Founder
Cathy (she/her) works with people and organisations to create inclusive, healthy and more productive workplaces that work for everyone.
A renowned leader, speaker and communicator, Cathy blends curiosity and empathy with deep cross-sector experience. She prides herself on helping people move out of stressful situations to create human-focused workplace cultures where compassion and connectedness – and people – are encouraged and valued.
Cathy has led organisations across a range of industries including Engage for Success (the UK’s movement for Employee Engagement), and has helped to transform many more through her work as Capability Brown, and most recently at Management Geek.
Cathy carries her personal experience of neurodivergence into the solutions she co-creates with her clients, through conversations, commitment and curiosity - helping them to manage themselves and their teams in ways that work for everyone.
13:40 - 14:00
Exinity Case Study: Freedom! How a Seismic Change in Our Wellbeing Offering Led to Unexpected Results
We knew we had some major work to do on this offering in order to attract and maintain the talent we needed.
With backing from the top, a brand-new wellbeing offering was rolled out over the next 24 months. Using Exinity’s mission ‘Freedom to Succeed’ as its hook, this new offering aimed to empower our people and support them across multiple aspects of the employee lifecycle.
The results? Some, such as more engaged colleagues, we had anticipated. But some, such as the financial impact the offering led to, and becoming recipients of an award for ‘Best Wellbeing Strategy’ were unexpected bonuses…..
Speaker:
.png?width=200&name=Wendy%20Murphy%20(2).png)
Wendy Murphy
ExinityVP Corporate Communications
14:00 - 14:20
Appreciation in Action: 2024 Trends That Create a Positive Culture for a Productive Workforce
Explore the pivotal role of appreciation in fostering a positive workplace culture and driving employee engagement. Through BHN's latest research insights, you will gain valuable knowledge on enhancing employee morale, productivity, and loyalty. From understanding the symbiotic relationship between culture and employee experience to designing personalised benefits and rewards programmes, you will leave equipped with practical tools and actionable ideas to transform your organisation into a vibrant, thriving workplace.
We will cover:
- The interconnectedness of culture and employee experience, and its influence on organisational success
- The impact of employee appreciation on morale, productivity, and loyalty
- Actionable strategies and resources to design tailored benefits and rewards programmes that align with employee expectations and enhance talent attraction and retention
Speaker:

Chris Ronald
Blackhawk NetworkVP B2B EMEA
Chris is accountable for accelerating and enabling growth by creating high-performance teams and functions that work to scale the business. After holding leadership roles across both public and private companies for national and global brands, Chris has a wealth of experience when it comes to general management, sales & marketing, client success & service and operations. As a result, Chris is able to achieve strategic transformation and drive profitable B2B growth strategies for Blackhawk Network and its customers.
14:20 - 14:40
Rspca Case Study: Creating an Award-Winning Wellbeing Strategy
Speaker:

Jeremy Gautrey-Jones
RSPCAAssistant Director Employee Experience
15:00 - 15:30
Coffee & Networking
14:40 - 15:00
Uber for Business: Fostering a Collective Company Culture That Still Caters to Individual Tastes
UK workers have never been more motivated by personal values than they are right now. As an increasing number of Gen Z-ers enter the workplace, they want to work for a business that understands them. This requires a better work-life balance and a greater sense of belonging that goes beyond the typical 9 to 5. This is set against a backdrop of default hybrid working arrangements which are creating more dispersed teams than ever before.
So how do businesses continue to nurture strong company cultures and team relationships while navigating a workforce that also values individuality? This talk will explore how businesses can tailor employee benefits to foster a stronger sense of community while also giving individual employees a sense of choice. This is where the food and travel perks, including ‘bleisure’ trips, come into their own by bringing teams together while offering individuals the flexibility to make their own decisions. Perks that allow employees to bring their personal values into the workplace will be key to an engaged workforce.
This talk will cover:
• Employee engagement challenges as we navigate a more hybrid workforce
• How Gen Z-ers bringing their personal values to work are shaking up workplace culture and benefit schemes
• How companies can adapt their benefit schemes to offer perks that bring people together while valuing their individuality
• The role of food and travel to bring teams together
• The importance of ‘bleisure’ travel in creating a more connected and engaged workforce
Speaker:

Jenna Brown
Uber for BusinessHead of Uber for Business, UK
11:00 - 12:00
Connecting Employees to Your Companies Social Impact Mission
Speaker:

Evan Rhoda
BlackbaudPrincipal, Corporate Solutions
11:00 - 12:00
Learn How Your Employees’ Experience Stacks up Against the Highest-Performing Companies
Join Firstup's interactive workshop to discover how far along the journey to a truly engaged workforce your organisation really is and how you can push forward to an adaptive experience that in turn will deliver lower attrition and higher productivity.
Alice Boyd, Lead Consultant, Comms Strategy and Ulus Isa, Solutions Consultant will ask the searching questions about the reach, delivery, personalisation and insights of your current communications, and demonstrate how the Firstup platform offers the ability to enhance outcomes through:
- Audience segmentation, and AI-powered delivery.
- An employee interface that serves, but more importantly surpasses the needs of a simple modern intranet.
- Powerful analytics that not only illustrate engagement but also give actionable insights.
Speakers:

Alice Boyd
FirstupLead Consultant - Communications Strategy
Creative communications professional with a passion for people, storytelling, brand and culture.
I'm now partnering with Firstup customers to help drive adoption and engagement throughout their digital employee experience journeys. This includes reaching 100% of their workforce to drive business initiatives, boosting morale through employee recognition, and leveraging data insights to inform business decisions.
I've worked in various sectors in both New Zealand and the UK, including technology, utilities, and healthcare. Some of my specialties include internal engagement, digital employee communications, and stakeholder management.

Ulus Isa
FirstupSolutions Consultant
13:40 - 14:40
Practical Solutions for Combating Financial Stress and Enhancing Employee Wellness
Gain valuable insights into practical strategies and sustainable solutions that can not only improve employee wellness but also reduce absenteeism, increase engagement, and ultimately boost employee performance.
Speakers:

Debbie Events
PluxeeClient Service Manager

Connor Roche
PluxeeBusiness Development Manager
Connor is passionate about employee benefits and wellbeing. Dedicated to enhancing workplace satisfaction and productivity through tailored solutions. A trusted advisor with a focus on holistic employee wellness.
“This was one of the best events I have been to. There were so many great speakers and I have taken away so much that I can feed into our processes. I would definitely recommend the event and will certainly be going again. Thank you to everyone who made this possible”HR Manager, CPS
.png)
“Good opportunity to meet relevant suppliers/providers, and a lot of very interesting speakers and sessions. I wish someone else from my organisation had been able to attend as I wasn't able to cover everything I wanted to see!”Communication Business Partner at Air France

“Super line up, great venue and free. So wonderful to collaborate and meet fellow IC peeps!”Head of Internal Communications & Engagement, Alzheimer's Society

/Zendesk.png)
It scales to meet the needs of any business, from startups and small businesses to growth companies and enterprises. Zendesk serves businesses across a multitude of industries, with more than 125,000 paid customer accounts offering CX and EX service and support in more than 30 languages. Headquartered in San Francisco, Zendesk operates worldwide with 15 offices in North America, Europe, Asia, Australia, and South America.

Our neuroscience based platform helps organisations measure the key employee engagement AND happiness drivers to power their people strategy.
Want to know how we can help guide your organisation to better retention, cultural alignment and performance? We have the answers… Visit us on Stand 21.

 Firstup is led by a team of enterprise software veterans from two legacies, SocialChorus and Dynamic Signal, who believe in the promise of new technology and the power of people-driven business transformation. Using our powerful orchestration engine, we bring personalised information and systems access to every employee where they are—on any endpoint or device, in any language, anywhere in the world. Whether they’re wired, mobile, frontline, distributed or essential, FirstUp gives employees what they need to do their jobs efficiently, and companies what they need to achieve agility. That’s how we help enterprise customers like Amazon, ABInBev, Ford and GSK continue to transform their businesses.
Firstup is led by a team of enterprise software veterans from two legacies, SocialChorus and Dynamic Signal, who believe in the promise of new technology and the power of people-driven business transformation. Using our powerful orchestration engine, we bring personalised information and systems access to every employee where they are—on any endpoint or device, in any language, anywhere in the world. Whether they’re wired, mobile, frontline, distributed or essential, FirstUp gives employees what they need to do their jobs efficiently, and companies what they need to achieve agility. That’s how we help enterprise customers like Amazon, ABInBev, Ford and GSK continue to transform their businesses.
 Achievers’ employee voice and recognition solutions bring your organisation’s values and strategy to life by activating employee participation and accelerating a culture of performance. Achievers leverages the science behind behaviour change, so your people and your organisation can experience sustainable, data-driven business results.
Achievers’ employee voice and recognition solutions bring your organisation’s values and strategy to life by activating employee participation and accelerating a culture of performance. Achievers leverages the science behind behaviour change, so your people and your organisation can experience sustainable, data-driven business results.

Visit Website
We help you create communication and learning campaigns to deliver positive change.
Whatever you need employees to do, we partner with you to prompt the actions that will have the greatest impact - to shape the moments that matter.
Drawing on approaches from behavioural science and advertising, we reinvent communication formats into campaigns that support real change.
Our experienced consultants partner with you to build insight into how to achieve the impact you need. We bring the digital and creative skills to identify, design and deliver solutions from comms campaigns to music videos, workshops to animated movies, interactive digital experiences or something else altogether.
Whatever your business needs, drop us a line to chat about how we can help.
Follow us on Linkedin and Facebook.
/Poppulo-1.png)
Poppulo is the leading communications and workplace experience software company. The Poppulo Harmony platform helps enterprise organizations achieve more by effortlessly connecting their employees, customers, and workplaces through omnichannel employee communications, digital signage, and workplace management. Poppulo's 6,000+ customer base is representative of the world's most successful companies, including 47 of the Fortune 100. Follow Poppulo on LinkedIn and on X.

/Interact-1.png)
Interact provides enterprise-grade intranet software that transforms the way businesses communicate. Our mission is to inform and connect every organization's greatest asset: its people.
Interact serves over 1,000 customers and millions of employees. For more than 15 years, we have worked with leading organizations like Domino’s, Subway, Levi Strauss & Co. and Teva Pharmaceuticals to deliver outstanding intranet experiences.
Please come and see us in the exhibition area to discover how we can help you to create a thriving, connected workforce.
Contact: E: info@interactsoftware.com
 LumApps is a global Employee Experience Platform, transforming how companies engage, enable and empower their workforces. The cloud-native solution is architected to tailor each experience to the individual needs of each employee. With an industry-leading employee data layer to drive next-level personalization, LumApps can deliver truly tailored communication campaigns and orchestrated employees journeys that help attract and retain great talent. Some of the world’s biggest companies – including Capital One, LVMH, Stellantis and Publicis Sapient – rely on LumApps to build strong cultures, promote knowledge sharing, and provide a performance-boosting employee experience. Learn more at www.lumapps.com.
LumApps is a global Employee Experience Platform, transforming how companies engage, enable and empower their workforces. The cloud-native solution is architected to tailor each experience to the individual needs of each employee. With an industry-leading employee data layer to drive next-level personalization, LumApps can deliver truly tailored communication campaigns and orchestrated employees journeys that help attract and retain great talent. Some of the world’s biggest companies – including Capital One, LVMH, Stellantis and Publicis Sapient – rely on LumApps to build strong cultures, promote knowledge sharing, and provide a performance-boosting employee experience. Learn more at www.lumapps.com.

Gate One is a leading digital and business transformation consultancy focused on designing and delivering meaningful change for some of the world’s most interesting, innovative and influential organisations.
Our customer experience specialists work closely with the C-suite and extended leadership teams across FTSE companies and private businesses to conceive and deliver the big, customer-focused ideas that will transform their organisations. This includes tackling their toughest challenges and accelerating their boldest ambitions, helping them to achieve lasting change and results.
Our deep, cross-sector experience provides us with extensive market knowledge, which we use to help inform and shape our clients’ thinking. We also share our expertise more widely through regular, published insights.
Trust us to embed meaningful and lasting change across your business and for your customers.
/Blackbaud-1.png)
Two of our solutions allow businesses to create meaningful social impact. EVERFI from Blackbaud powers social impact through education for purpose-driven organisations. YourCause from Blackbaud provides essential software for companies to connect their employees to the nonprofit community.
Together, we can make a difference.
/Forty1-1.png)
With more than 50 people across 2 continents, we bring a unique combination of people, skills and life experiences to our clients’ challenges. Our purpose is to create experiences that enrich working lives.
What makes Forty1 different? We bring insight, creativity, and tech know-how to every challenge, but four things set us apart:
- An industry-leading Behavioural Science Unit, ensuring that our work makes the right impact on human thinking and behaviour.
- A specialist Employee Listening capability, using leading-edge digital tools to create safe spaces for employees to tell us what they think and need.
- Learning & Capability Development Expertise that enables us to help your leaders, managers, and employees build the knowledge and skills they need to make change happen.
- A world-class Live, Virtual, and Hybrid Events team who deliver memorable experiences that inspire change and engagement.
/Culture-Amp-1.png)
/Contact-Monkey.png)
Internal communications email software that integrates seamlessly with Outlook & Gmail
/Unily-1.png)
/BlackHawk.png)
/Workshop%20logo%20clipped.png)
Create exceptional internal communication and marketing campaigns that are always relevant, engaging, useful, and on-brand. We replace any internal email tool you have, and integrate with the other communication channels you use the most (including Slack, Sharepoint, Microsoft Teams, and more).
With Workshop, you can:
- Quickly build beautiful internal emails: You have all the creative resources you need to design and create great employee emails in one place with our drag-and-drop design tools and swappable templates.
- Always send to the right audience at the right time: We automatically sync up with your employee data sources (like Active Directory or your HRIS), so it’s easy to send and segment your messages.
- Measure and improve your efforts: Track opens, clicks, read time, and see exactly who is engaging with the email (so you can decrease noise and increase results).
/Namecoach%20logo%20clipped.png)
/Pluxee.png)
The leading global employee benefits and engagement partner that opens up a world of opportunities to help people enjoy more of what really matters
We believe that living life to the full means making the most of every moment and sharing experiences with the people we care about. To make these experiences meaningful, fulfilling, and personalised, we combine our 45+ years of experience with the agility and energy of a new digital brand. The result is an exciting mix of 250+ products that give employees more freedom in the choices they make every day across 31 countries – from restaurant meals to culture, incentives, and gift vouchers.
/Uber%20for%20Business%20logp.png)
/Klaxoon.gif)
Klaxoon is the world's first all-in-one work collaboration experience platform that turns every interaction into a concrete business win. With 10 powerful visual collaboration tools, Klaxoon is a game-changer that empowers individuals to increase engagement, drive productivity, and shape an innovative workspace. Through its world-class integrations with popular tools like Microsoft, Google, Jira and Zapier, Klaxoon brings teams together, igniting creativity and delivering concrete results. Klaxoon enables thousands of users from over 7,500 corporations, NGOs, universities, and public administrations, as well as 15% of Fortune 500 companies. Klaxoon empowers a diverse range of organizations to enhance collaboration, improve productivity, and achieve their strategic goals.
/Deliveroo-for-Work.png)
Deliveroo for Work is on a mission to boost employee wellbeing through great food. We make your life easier with a simple food-spending solution for your business, meaning freedom from the stress of expense reports and the ease of one monthly invoice.
Your employees order through Deliveroo from thousands of best-loved restaurants and grocery partners. From team lunches to meal allowances and late-night working we've got them covered, whilst giving you access to a corporate portal where you can customise your account and gain insights into employee spending.
Deliveroo for Work operates across 8 markets, including Belgium, France, Hong Kong, Italy, Ireland, Singapore, the United Arab Emirates, and the United Kingdom.
Visit our stand and book a demo.
/YuLife.png)
/Blink-New.gif)
Founded in 2015 and with offices in London, Boston and Sydney, Blink is a Leader in the G2 Grid® for Best Employee Engagement Software and named in the 2022 Deloitte Technology Fast 50.
Joinblink.com
/Sideways6.png)
/Engage%20Solutions%20Group.png)
/LearnAmp.gif)
Learn Amp is the complete People Development Hub. Weaving together learning, community, and talent development to power performance. Enabling modern companies to balance people-led and company-led learning, and align individual progression with collective goals. Technology on its own is not a silver bullet. Get software with a service (SwaS) through our expert coaching and advisory services. Our consultative approach has led to a 96% retention rate of happy customers. Speak to us to find out more and join future-thinking organizations like Metro Bank, GAIL's Bakery and Specsavers in consolidating and replacing their tech stack with Learn Amp
VENUE DETAILS
The Brewery
52 Chiswell Street, , London EC1Y 4SD


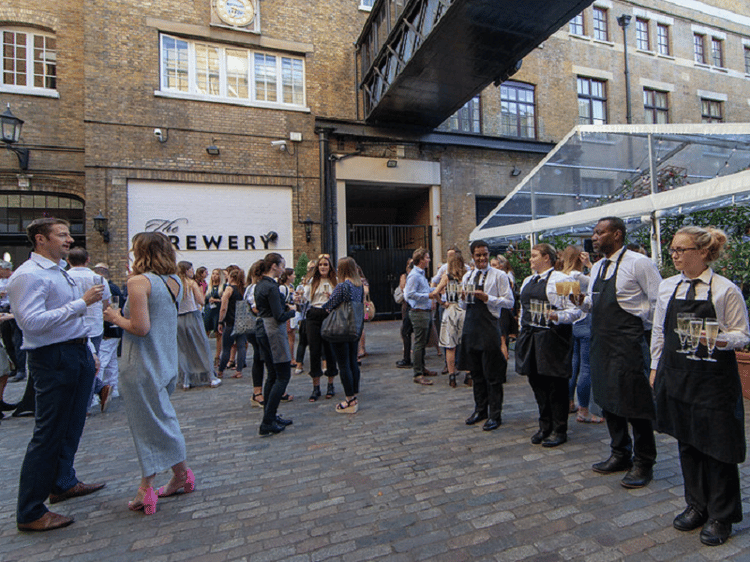

HOW TO GET HERE
Take the Northern Line towards Morden on the London Underground
Depart at Moorgate Station
Walk north on Moorgate/A501 for 7 minutes
Turn left on to Chiswell St
The Brewery will be on your left

Take the Heathrow Express to Paddington Station
Take the Elizabeth Line on the London Underground towards Abbey Wood
Depart at Liverpool Street Station
Walk West on Liverpool Street
Turn left onto Eldon St
Continue straight on South Pl, Ropemaker St and Moor Ln
Turn left onto Chiswell St
The Brewery will be on your left

Take the Thames Link towards Cambridge
Depart at London Bridge
Take the Northern Line on the London Underground towards High Barnet
Depart at Moorgate
Walk North on Moorgate/A501
Turn left onto Chiswell St
The Brewery will be on your left

Take the Stansted Express to Liverpool Street Station
Head South toward Liverpool St
Turn right onto Liverpool St
Turn right onto Broad St
Turn left onto Eldon St
Continue onto South Pl, Ropemaker St and Moor Ln
Turn left onto Chiswell St
The Brewery will be on your left

TICKET OPTIONS
EMPLOYEE ENGAGEMENT LEADER
-
Are you a senior leader in the employee engagement space?
-
Do you make decisions?
-
If the answer to these is yes then you meet the criteria for a 'Leaders' ticket...
-
Single Ticket
-
5 Halls of Case Study Content
-
Event Networking
-
Interviews
-
Panel Debates
-
1-2-1 Meetings
-
Focus Groups
-
Lunch & Refreshments All Day
-
After-Event Drinks
-
Note: Registrations are subject to approval
Single Ticket
-
Single Ticket
-
Free Ticket Applicable for Senior Individuals Working in Employee Engagement
-
Not Relevant to Suppliers/Vendors to the Industry
-
5 Halls of Case Study Content
-
Event Networking
-
Interviews
-
Panel Debates
-
1-2-1 Meetings
-
Focus Groups
-
Lunch Provided
-
After-Event Drinks
-
Registrations are subject to approval
Supplier Ticket
-
For Suppliers
-
5 Halls of Case Study Content
-
Networking and Commercial Opportunities
-
Event Networking
-
Interviews
-
Panel Debates
-
Lunch Provided
-
After Event Drinks
-
Registrations are subject to approval
£1,495+VAT
INTERESTED IN ATTENDING THE EMPLOYEE ENGAGEMENT SUMMIT?
Download the event brochure.



/Vaibe.png)
